Website Security
Two security methods for protecting your websites are available in Circle:
-
HTTPS protocol - Encrypts communication between the browser and the website.
-
User authentication (SecURL) - Protects access to recipient information stored in content objects.
For an optimal security solution it is recommended that you use HTTPS protocol, User authentication and Secure ID.
HTTPS protocol
Use the HTTPS protocol to ensure that communication between the browser and the website is encrypted. When a user connects to a website via HTTPS, the website encrypts the session with a Digital SSL (Secure Sockets Layer) certificate.
When HTTPS is configured and activated, Circle enforces HTTPS in webpage links, friendly URLs, XMPL APIs and Circle Live Preview. Currently HTTPS is not supported in email, PDF on demand and XMPieRURL content object. If you wish to continue using HTTP in email and PDF on demand in an HTTPS configuration, you can do so by leaving port 80 open.
In an HTTPS configuration there is no automatic blocking of HTTP. For example, if a custom website link is hard coded as HTTP, it will continue to work in HTTP.
After you enable HTTPS for a specific project, the XMPL server URL in the website configuration file (xmpcfg.js) changes from HTTP to HTTPS. Therefore, you must download this file and replace it in the site root folder. If you switch back to HTTP, replace the configuration file as well.
Note: Before activating HTTPS, refer to the HTTPS configuration prerequisites article.
To activate HTTPS protocol:
-
In the library, click Website on the left pane.
-
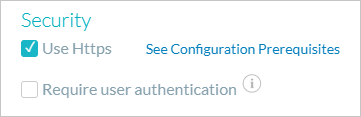
In the Security section, select the Use HTTPS checkbox.
-
Click Save.
-
In the General Configuration section, click the Download
 icon to download the newly generated configuration file (xmpcfg.js)
and replace it in the site root folder.
icon to download the newly generated configuration file (xmpcfg.js)
and replace it in the site root folder.
User Authentication - SecURL
Important! Before starting, it is recommended to watch the following video: Authentication on personalized websites.
Prerequisite: Prior to enabling user authentication in Circle you must add authentication components to your XMPL site to support user sign-in. Learn how
User Authentication protects unauthorized users from accessing private recipient information which is stored in content objects.
User Authentication is used to increase online security. Protecting your Personalized URLs (PURLs) in this way is an important step towards GDPR compliance, and is typically used in conjunction with HTTPS.
When using User Authentication, the system prompts the recipient, when trying to access a personalized URL, to sign in via a login page. The recipient must enter a password (or a user name and password, depending on the setup). If the password is correct, the recipient is granted access to the PURL. Access to read/write content object values will always be protected until the recipient signs in. Event tracking will not work until the user is signed in.
Once User Authentication is enabled in Circle, all XMPL Rest API calls will require a security token for the project, and the site will not work without user login.
User Authentication is implemented on a project level, and affects both managed and custom websites.
The out-of-the-box authentication methods provided are No Hashing (clear text) and MD5. On insert and update, the password content object is encrypted according to the hashing method.
Several technical points regarding User Authentication:
-
Once User Authentication is enabled in Circle, the XMPL site for this project will not work without user sign-in.
-
When User Authentication is enabled, all XMPL Rest API calls to this project will require a security token.
-
In order to redirect to the sign-in page, you must create a separate config file on the client called xmpcustom.js. To create this file, see Setting up the xmpcustom.js File.
-
In order to know which user to authenticate, the RID must be passed in the PURL.
-
The login session time out is one hour, after which the user is returned to the sign-in page.
-
XMPL version 3.0 or higher is required.
Note: SecURL is not supported in Template-Instance and Campaign-on-Demand (uStore).
To activate User Authentication
-
Make sure you have added authentication components to your XMPL site to support user sign-in.
-
In the library, click Website on the left pane.
-
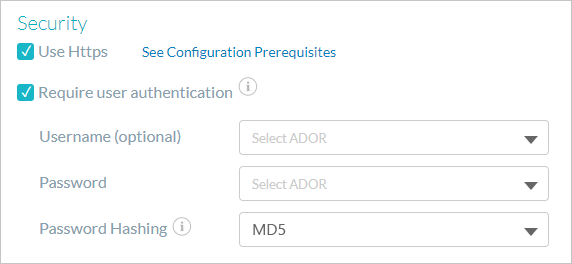
In the Security section, select the Require user authentication checkbox.
Note that additional fields are added below.
-
From the Username and Password dropdown lists select text content objects. Username (for example First Name) is optional. Password can be a content object that represents an ID, a login code or a password content object (a given customer password).
-
From the Password Hashing list select the required password hashing method. The available methods are MD5 and No hashing.
Make sure that your hashing selection is compatible with the method applied to the passwords in your recipient list.
If you wish to use a more complex hashing method, contact request@xmcircle.com.
Change the password hashing method
In order to change an existing SQL password column from clear text to MD5 encryption you can use the following script:
Note that once you run the script you cannot go back to clear text. It is recommended to back up the database before running the script.
-- Run once:
createfunction dbo.XMPieHashMD5 (@input VARCHAR(250))
RETURNSVARCHAR(250)
ASBEGIN
DECLARE @ret VARCHAR(250)
set @ret =(SELECT
CAST(N''ASXML).value(
'xs:base64Binary(xs:hexBinary(sql:column("bin")))'
,'VARCHAR(MAX)'
) Base64Encoding
FROM(
SELECTHashBytes('MD5', @input)AS bin
)as x);
return @ret
END
--Usage example - Update:
updatedbo.[table]
set[Column] = dbo.XMPieHashMD5([Column])
